In keeping with the fact individuals and enterprises are seeing and experiencing a lot more occurrences of ransomware, I’m also seeing a lot of articles and comments either discussing it and what to do about it or providing some siloed indicators of where ransomware might go.
A number of comments, in my opinion, are aimed at what ransomware has been up until now and how to combat it. Very soon, few if any of these suggestions are going to be effective in stemming the tide of ransomware. It’s my opinion that ransomware is already exhibiting some horrifying variations that we aren’t taking into consideration fast enough.
To Really Protect, Think Like a Criminal
It’s not a coincidence that some of the best minds out there when it comes to really understanding IT Security and how to actually address risk and stop these types of well-conceived and formed attacks come from those who lived on the dark side and have come to the light – former hackers like Kevin Mitnick, Robert Morris, and others. And we have a lot of white hats (too many to name here) who are extremely good precisely because they (a) think the same way as the criminal black hats and (b) have incredible intimate technical knowledge just as black hats do.
And don’t think your servers are safe. Hackers are already looking to get inside of your data center and maliciously encrypt and hold for ransom as much of your company as they can.
In order to effectively handle some of these malevolent attacks, you can’t be standing still. The whole history of dark-side hacking, breaches, and generalized wreaking of havoc paints a storied picture of never standing still. Because once something is proven as technically possible, the very next thought by highly sophisticated hackers is instantly “How can this be extended?!”
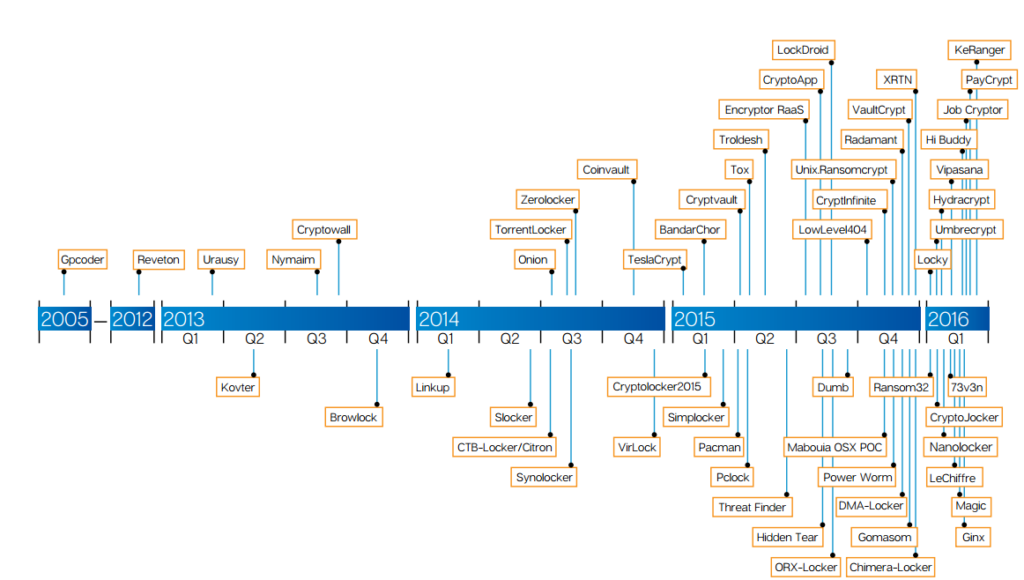
Almost all hacks start out as “let’s try something” attempts. Initially even conceiving of a new vector often takes intimate and expert knowledge of the target (usually operating system, but sometimes a target language flaw or other type of architecture). But once a potential vector is exposed as having validity, it’s game on. There’s the initial hack, and then all the “mods” (modifications) that go with it come like a flood. (Reference the attached graphic associated with this article.)
Ransomware is no different. Just when you think you’ve got the attack scheme and the attack vector figured out, so many mods are hitting you, it makes your head swim. I’m seeing some articles, well-meaning, that state “if you just do this, this and this, you can stop ransomware.” If you do those things, yes, you can stop the ransomware of today or the ransomware of last week. But you won’t be doing much to stop the ransomware of next week or next month or that’s coming out in three months.
Hackers are always thinking fifteen steps ahead. It’s time we started doing the same. Here are some things to “look forward to” and expect when it comes to ransomware. A lot of these mods are already in the wild! But if they are not, you can be sure, hackers are already working on these:
Types of Encryption
In terms of “types of execution” – that is, “the what” or specifically what data hackers are going to start targeting. Here are some types you can be expecting. Hackers know… the more data they can encrypt and hold hostage, the more money they can legitimately extort.[1]
Like almost all models of malware and other codified threats to the enterprise environment, hackers follow a great model – start small and grow from there. Ransomware started out as solely an endpoint threat. It’s naturally going to progress from there and already has.
The broadest statement I can make is to say, pretty much everything you have attached to an endpoint is going to end up being fair game:
(1) Encryption of backups. We’re already hearing about variants of ransomware that are specifically aimed at thwarting and foiling so-far-advanced recovery strategies around keeping backups. Hey, if your backups are attached such as a drive hanging off your Macintosh endpoint intended to run Time Machine, you could be (and probably will be) hosed. TechRepublic and others are reporting the KeRanger ransomware now attempts to encrypt your backups. So much for that idea. So for backups that are locally accessible as well as accessible over the network (which most enterprise backup software leverages some kind of network-attached storage)… beware. “Having good backups” as a mitigation strategy is already under attack by the dark side and will continue to be more so in 2016.
The mitigation here is likely some kind of logical or actual air gap where backups, once taken, are made immediately unavailable from a network standpoint and can only be brought back online for specific backup requests. Think something like Amazon Glacier where backups aren’t immediately accessible and must be specifically requested and brought back online later.
(2) Encryption of network shares. This is really an extension of the backup problem above. As I said, anything that is network accessible is already free game for a number of ransomware variants that are already doing this. Expect this to be a catchup exercise in 2016. Most ransomware will attempt to reach out and encrypt whatever it can find on network attached shares, be they CIFS- or NFS-based shares.
The mitigation for this is going to continue to be strong access controls on network shares, but even this strategy will only hold up for so long. I’ll discuss this more below when I talk about ransomware execution models below.
(3) Encryption of cloud shares and cloud-attached end-point storage. Same thing. Whatever you have attached is going to become a target for advanced mods soon coming out in the ransomware arena.
Do you rely on Box Sync? Dropbox integration? OneDrive? S3? These are all vectors that are going to be touched, explored and encrypted if possible. Yes, a lot of these cloud storage points rely on synchronization mechanisms such that data is mirrored between the client computer and the endpoint storage systems in question. So encryption of your Box or DropBox content, for instance, can or could be recovered from Box or DropBox if you’ve caught the process in time. But are you going to catch it? If you don’t, your own client machine will start replicating encrypted and ransomwared data into cloud storage endpoints. This would already be an issue for client machines tightly coupled to those cloud storage endpoints with cached credentials.
(4) Encryption of Virtual Private Cloud storage. Most if not all of the main players in the cloud offer virtual private clouds that allow small, medium, and large businesses to build out a privately accessible infrastructure in public clouds accessible from an internal private network. But again, if it’s attached, it’s going to end up becoming fair game and from an endpoint perspective, if your PC has access to these areas in ways that look normative to the operating system such as networked drives, accessible UNCs, etc., it’s there for the taking. No real modifications are necessary other than to make the ransomware network share aware.
(5) Encryption of metadata and boot-level/block-level lockout and encryption. Again, here hackers have gotten more brazen. Instead of encrypting your files in stealth, behind the scenes, at least one ransomware, Petya, took a really brazen approach and infected the Master Boot Record (MBR), thereby disabling the endpoint client computer from booting into any recognizable operating system and having malware detection available to possibly detect this. (An attempt to deceive the endpoint user is made by putting up a CHKDSK screen and indicating the hard drive is being checked for errors while in fact encryption is taking place behind the scenes.)
Metadata (file names, sizes, dates, etc. – information about files and file contents) is also already under attack with some variants already encrypting or obfuscating file metadata. This is done so you can’t identify what was encrypted and being held and further ups the game when it comes to combating this threat. (Essentially what files do you know to restore from backup if you can’t even read the file names?!)
The broadest statement I can make is to say, pretty much everything you have attached to an end point is going to end up being fair game.
I expect to see more attacks like this where the “how” (files, master boot record attacks, metadata, etc.) and not the “what” is reinvented in numerous ways in ransomware to be released soon into the wild.
And don’t think your servers are safe. Hackers are already looking to get inside of your data center and maliciously encrypt and hold for ransom as much of your company as they can.[2] Read on in the next section below for more here.
Execution Models
So in 2016 and beyond, expect ransomware to vary in at least the following ways as it relates to the execution of the encryption and holding for ransom – the “how” and not the “what”:
(6) Execution within an elevated context. Right now, most ransomware runs in what we call “the context” of the infected user. A user is sent a malware link in an email, he or she clicks on it, and then this starts the ball rolling in terms of the execution of the code that starts encrypting your data. The encrypting happens as that user.
But as we’ve seen in breach after breach at the enterprise level, expect ransomware to start getting smart about checking to see if elevated access is achievable within a given timeframe before setting to work on encrypting data. If the elevation of access can be achieved through known vulnerabilities in standard desktop and even server operating systems, then this tact will be taken as it allows more data to be accessed and encrypted. A lot of users at home already have full administrative privileges on their laptops and desktops, so this is generally not a problem – running in the context of the user is the same as having administrative privileges to the laptop or desktop itself.
Hackers are always thinking fifteen steps ahead. It’s time we started doing the same.
In an enterprise environment, however, running in user context provides limited access to data, especially across network shares (aside from the fact enterprises still don’t exercise good access control governance on network shares and servers and a lot of users have access to data they have no business having access to). So to gain access to as much data as possible, ransomware will come equipped to check and leverage known vulnerabilities to elevate access if it’s possible to do.
(7) Bootstrapping of encryption through other vulnerability vectors instead of reliance on infected links. Already we are hearing of attempts to find other ways to bootstrap the encryption code or to “gain context” (as we technologists like to say) to begin the encryption process. Look for ransomware in 2016 to spread from client endpoints and relying on users to click on malicious links to these attacks being launched through other vulnerabilities that allow for code injection and the bootstrapping of context through other means.
Conclusion
The game of ransomware is very solidly afoot. I saw one poster on LinkedIn today who stated we can starve ransomware out through vigilance around keeping backups, restoring those backups, and not paying the ransoms. Would that were going to be the case.
I predict this is only going to get worse before it gets better. We’ve got to be thinking fifteen steps ahead like those on the dark internet are already doing in order to fully and completely combat and ultimately defeat this threat. Ransomware is, in my opinion, one of the best conceived and most effective threats, both in the simplicity of execution as well as the potential for payout, as anything we’ve seen in the last 25 years.
I did not follow my normal editorial process when writing this article and flushed it out rather quickly in response to articles I read this weekend that lead me to believe we aren’t being imaginative enough and moving quickly enough to effectively stop this growing and maturing threat. So if you have comments, corrections, or other thoughts around this, please feel free to leave them in the comments section below or feel free to engage me on Twitter @ChrisEOlive.
Update: 6/24/2020
While I didn’t specifically call it out in this article, I did go on record shortly after while speaking during 2018 and onward as saying not only will ransomware not disappear, we will start seeing $1MM+ ransoms. Not only did that come true, but also RWaaS (Ransomware as a Service) became a thing specifically because of the dark web economy I called out here.
The industry will remain 20 steps behind until we adopt a hacker and “criminal mentality” when it comes to offensive and defensive cybersecurity. THESE types of approaches are not going to work:

____________________
Footnotes
[1] Some people are just waking up to the fact or still don’t fully realize the dark internet operates under its own “code of ethics” and business model. While hackers aren’t necessarily hiring statisticians and actuaries to get this down to an exact science, they do understand the basic concepts of gaming and benefit just like airlines employ for ticket pricing – how much can they ask in ransom that you are likely willing to pay, based on the value of the data they are holding ransom versus you looking at some dollar amount and exclaiming “No way! I’ll live without that data. I’m not paying that!” The more data they can hold for ransom, the more money they can extort and hence, the methods discussed in this article as well as probably others I haven’t laid forth will be considered, codified, and released on individuals and enterprises.
[2] I saw at least one article this week that claimed if you encrypt your data first, this will effectively block ransomware. This is incorrect and not the case! I actually help Fortune 500 enterprises encrypt and protect their data the world over and I can tell you emphatically, encrypting your data in advance will not protect you from ransomware. On servers on-prem and in the cloud, accessible through networked attached shares, our product can, if configured correctly, effectively block and prevent ransomware. But this is not done through the use of encryption, but through the use of strong access controls that modify and extend your operating system capabilities in ways that most malware authors probably aren’t thinking about, haven’t conceived of and they won’t be taking into account when writing their malicious code. And even if they were, they wouldn’t be able to circumvent the controls our product puts into place on your servers. Give me a jingle if you are interested in hearing more about this.